In this blog post, I describe the vpc-spoke-tgw OpenTofu module that simplifies the process of setting up networking for workload/spoke VPCs attached to a Transit Gateway (TGW). This module automates the creation of essential networking resources, including VPCs, subnets, route tables, security groups, DHCP option sets, and TGW attachments, facilitating integration with your organization’s hub-and-spoke architecture. This module leverages the terraform-null-label module to provide consistent naming for provisioned resources.
I recommend delivering OpenTofu modules as products, to enable other IT teams to use them autonomously.
An OpenTofu module for Hub-Spoke Deployments
The image below represents a typical hub-spoke architecture with the following:
Hub: An AWS account containing core infrastructure services (network ingress/egress, TGW, security appliances, shared services).
Spoke: An AWS account hosting a business application or workload with ingress/egress traffic from/to the Internet via the TGW
The hub shares its TGW with the spoke via AWS Resource Access Manager (RAM).
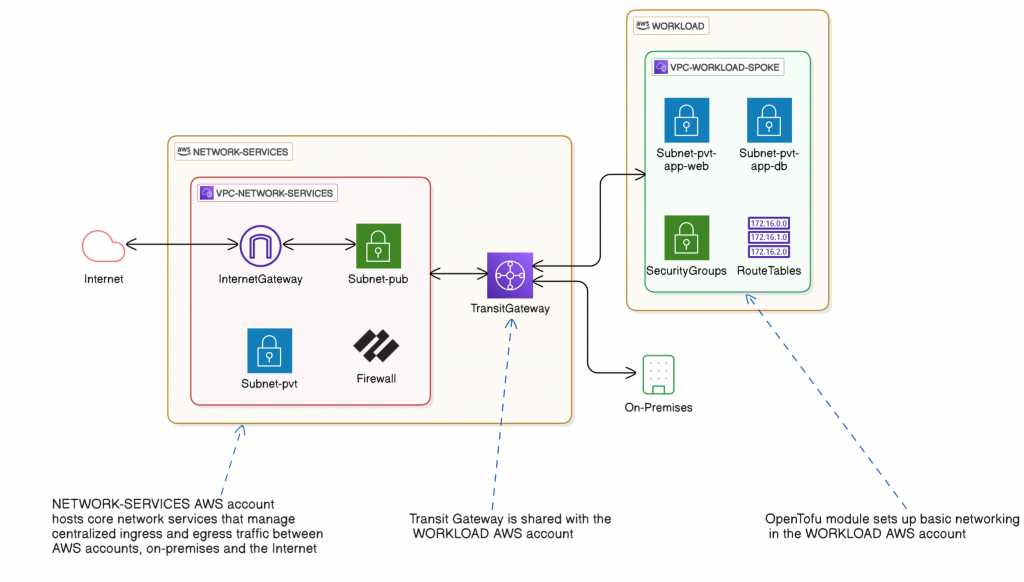
The vpc-spoke-tgw OpenTofu module accepts the TGW share invitation and sets up basic networking in the spoke (VPC, subnets, DHCP options, route tables with routes to the TGW, security groups).
Use Case: Setting Up Secure, Standardized Networking for a Multi-Account AWS Environment
Scenario:
Your organization has a multi-account AWS environment where the network team manages the central AWS account (hub), which includes the Transit Gateway (TGW), firewall configurations, and security measures like ingress/egress traffic management. The application teams manage their own AWS accounts, where they deploy various workloads (e.g., web applications, APIs, etc.) and need secure connectivity to other services within the company’s AWS and on-premises networks as well as to the Internet. In some organizations, infrastructure or platform teams may set up workload AWS accounts before application teams deploy their workloads.
To enable this, the application/infrastructure/platform teams attach their VPCs to the TGW shared by the network team. However, each team requires a standardized, secure, and automated way to create their VPCs and configure networking components like subnets, route tables, security groups, and DHCP options.
Solution:
The vpc-spoke-tgw OpenTofu module automates the networking setup in these workload VPCs that need to connect to the shared TGW. The module streamlines and standardizes the process, ensuring consistent and secure networking for each team.
Key Features of the vpc-spoke-tgw OpenTofu Module:
- VPC & Subnet Creation: Creates a VPC with private subnets distributed across availability zones, when multiple subnets are configured.
- TGW Attachment: Accepts the TGW share and creates the attachment of the newly created VPC to the Transit Gateway managed by the network team, ensuring proper routing and connectivity.
- Route Table Setup: Creates route tables with routes to the TGW for secure communication between the application’s VPC and other VPCs or on-premises systems via the Transit Gateway.
- Security Groups: Creates security groups to control inbound and outbound traffic based on application-specific needs.
- DHCP Option Set: Creates a DHCP option set for proper domain name resolution across the VPC.
- Parameterized Deployment: Can be used across multiple environments by using different input parameters or variables, specified in
.tfvarsfiles, thereby facilitating reusability, consistency and automation (CI/CD pipelines). - Standardized Deployment: Leverages the
terraform-null-labelmodule to provide consistent names for provisioned resources and allows for global tags, thereby facilitating adherence to naming and tagging standards.
Example Workflow:
-
Network Team: Shares the TGW with application teams via AWS Resource Access Manager (RAM), sets the necessary security configurations and provides CIDR blocks (reserved in IPAM) for use by application teams for VPCs and subnets.
-
Application Teams: Use the
vpc-spoke-tgwOpenTofu module to create their VPC and related networking resources (subnets, route table, security groups, etc.) with a simple configuration. The application teams can then deploy their applications into their networks an easily scale their networking (e.g., additional subnets, security groups) autonomously.
Benefits:
- Consistency: All application teams follow the same networking standards, simplifying management.
- Security: By automatically setting up secure VPCs, subnets, and security groups, the module ensures that networking is configured in accordance with your organization’s security policies.
- Efficiency: Application teams can focus on their workloads, while the OpenTofu module handles the repetitive networking setup tasks.
- Scalability: As the company grows and more application teams are onboarded, the module allows for easy and automated scaling of networking infrastructure without additional manual effort.
How to access the vpc-spoke-tgw OpenTofu module
You may access the module via any of the following:
GitHub – The module’s repo contains GitHub Actions workflows for CI/CD pipelines used for module testing as well as an example on using the module.
Conclusion
In this blog post, I demonstrated how you may use the vpc-spoke-tgw OpenTofu module to streamline the setup of networking for application teams while ensuring consistency, security, and compliance with organization policies. Try it out and feel free to provide feedback either as a comment on this blog post or as an issue in the GitHub repo. This is an example of how Platform Engineering teams may deliver IaC products for easy and autonomous consumption by application teams. There are many ways to deliver IaC products. You may provide access to the module via a Git repo, a UI, use TACOS software, etc., but you’ll need to pick an approach that works well for your environment (infrastructure, policies, practices, culture).
