-
Windows Management Instrumentation (WMI) is Microsoft’s implementation of Web-Based Enterprise Management (WBEM). It’s now part of Microsoft’s Windows Management Infrastructure (MI).
-
WBEM is set of standards developed to unify the management of distributed computing environments.
-
WBEM is maintained by the DMTF (Distributed Management Task Force).
-
Microsoft uses WMI to provide management data to the Windows Operating Systems as well as to other products (e.g. discovery and monitoring tools).
-
The management data provided by WMI on a computer may be accessed remotely from another computer, using clients or scripts, via DCOM/RPC or Windows Remote Management (WinRM)
Accessing WMI Data via DCOM/RPC
In order to access WMI data from a remote machine via DCOM/RPC, the client must have tcp/135 and tcp/49152-65535 connectivity to the remote machine (Windows 2008 and later). TCP port 135 is the RPC endpoint mapper port which will re-direct the client to one of the ephemeral ports (TCP ports 49152-65535) for obtaining WMI data from the Windows Management (winmgmt) service on the remote machine.
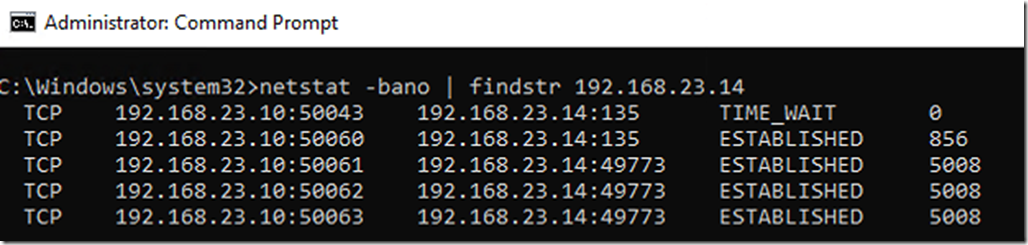
The screenshots below show WMI over DCOM/RPC access from client 192.168.23.10 to remote machine 192.168.23.14.
On Client:
Note that the client connects to tcp/135 and to tcp/49773 (an ephemeral port).
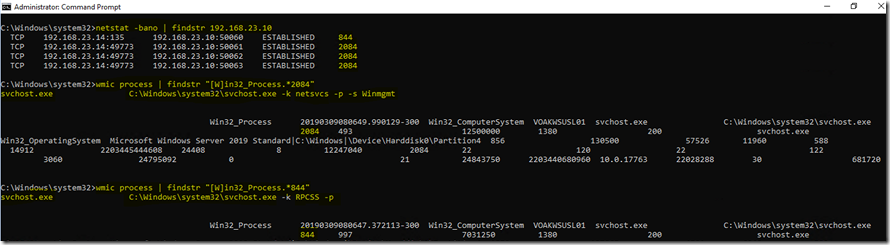
On Remote Machine:
Windows Operating Systems use a shared-service process svchost.exe (Service Host) to load various services from DLL files.
As you can see from the screenshot below:
The svchost.exe process running the RPC Endpoint Mapper service (RPCSS) accepts requests from the client on tcp port 135.
The svchost.exe process running the netsvcs sub-process for the Winmgmt (WMI) service accepts requests from the client on tcp port 49773.
NOTE: In order to avoid punching a big hole (tcp/49152-65535) through one or more firewalls, you may configure WMI on remote machines to use a fixed static port or smaller port range. Refer Setting up a Fixed Port for WMI.
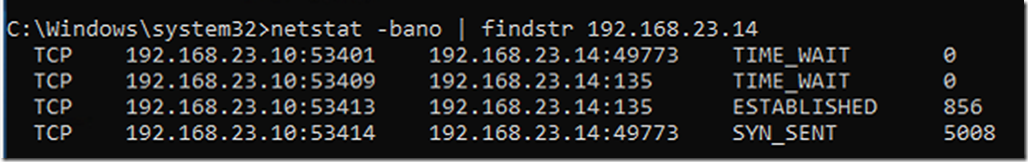
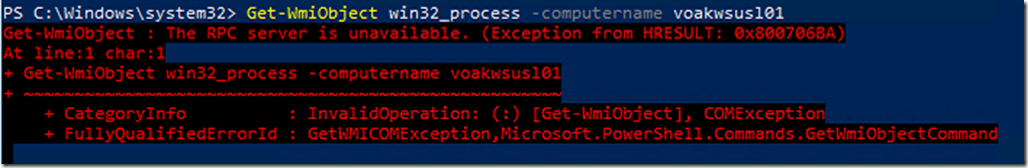
What happens if connectivity to the ephemeral ports is blocked?
If you are using the ephemeral ports for WMI and the client cannot connect to them, then the client will receive a “The RPC server is unavailable” error as shown in the following screenshots.
Accessing WMI Data via WinRM
-
WinRM is a more firewall-friendly method (SOAP-based WS-Management protocol) for accessing WMI data from a remote Windows machine.
-
WinRM can use a HTTP Listener (default) at TCP port 5985 or a HTTPS Listener at TCP port 5986 to process client requests. So, clients need to connect to only one of these ports depending on whether they’re using TLS or not.
-
WinRM also enables PowerShell Remoting (e.g. Invoke-Command)