VPN
Organizations usually use a VPN to provide secure remote working (working from outside the corporate network. e.g. home, airport) access for their employees. Typically, when connected to a Corporate VPN, all traffic leaving a remote worker’s managed device (laptop/desktop/mobile device owned and administered by the Organization) traverses the Corporate VPN tunnel into the Corporate network, from where it is routed to Internet destinations via the Organization’s perimeter firewalls.
CASB
With the explosive growth in the use of Public cloud SaaS applications (e.g. Office365, Salesforce, Pagerduty, AWS), Organizations have seen a growth in shadow IT as well as a bigger security threat (data loss, vulnerabilities, etc.). So, in order to mitigate or eliminate these issues, Organizations turn to Cloud Access Security Brokers (CASB). A CASB is an on-premises or cloud software that intercepts traffic between users and public cloud applications and applies relevant security policies (e.g. DLP, Threat management). CASBs may be deployed in a few modes.
REMOTE WORKING CHALLENGES
Poor User experience: As Organizations embrace the use of more Public cloud SaaS applications, a greater amount of end user traffic to Corporate applications (email, HR, Sales, Collaboration, etc.) is destined for a SaaS application over the Internet. So, when an organization’s remote workers are connected to a Corporate VPN, any Internet-bound traffic is hairpinned via the Organization’s infrastructure as shown in the image below (for a fictional Organization called Gruboom), thereby traversing a sub-optimal network path to the trusted Public cloud service (e.g. Office365) and increasing latency leading to a poor user experience. This problem is exacerbated for real-time media traffic (audio/video) for applications such as Skype and Microsoft Teams as such traffic suffers from jitter and poor quality when traversing encrypted tunnels.
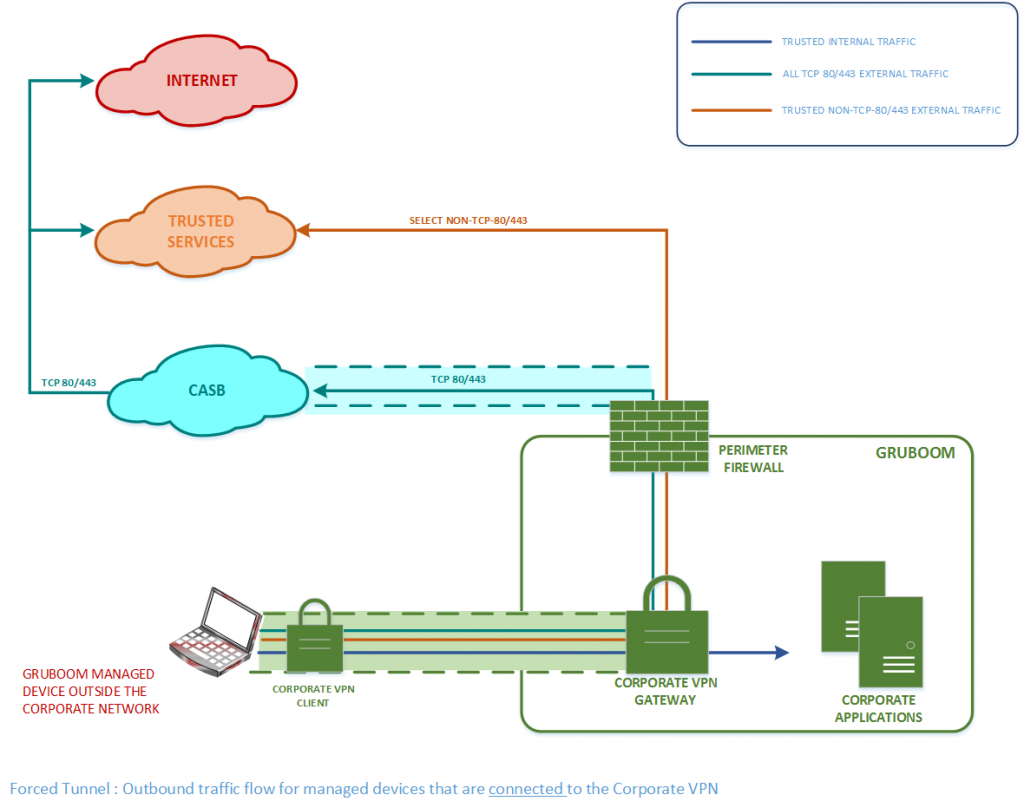
Security: The major Public clouds (AWS, Azure, GCP) use globally-distributed edge networks to optimize the network path from users to their cloud-hosted applications and minimize latency. In order to leverage these capabilities for remote works, Organizations should be able to steer Internet-bound traffic directly out of the user’s local Internet connection, rather than traverse the Corporate VPN. However, doing so does not subject the Internet-bound traffic to the same security policies as traffic that traverses the Corporate VPN.
COMETH COVID-19, COMETH THE SPLIT TUNNEL
The COVID-19 pandemic forced most Organizations to mandate most of their employees to work remotely thereby leading to possibly the highest number of concurrent remote workers ever experienced by Organizations. This brought the remote working challenges explained above, to the forefront and additionally led to an increased load on Organizations’ Infrastructures. So, many Organizations have rushed to implement solutions to address these issues and keep their employees’ productivity high.
Implementing a Split Tunnel with CASB
As my organization uses a Corporate VPN (forced tunnel) and a CASB for Web DLP (tcp/80 and tcp/443 Internet traffic), we decided to use a reverse split tunnel on our Corporate VPN (exclude certain traffic from traversing the Corporate VPN) in combination with our CASB (CASB client’s tunnel on managed devices) to steer traffic along 3 paths from a managed device as follows (and shown in the image below):
- Latency-sensitive trusted traffic (e.g. Office365) via the CASB tunnel from the remote worker’s managed device.
- Real-time media traffic (Skype/teams audio/video) via the user’s local Internet connection.
- All other traffic via the Corporate VPN tunnel.
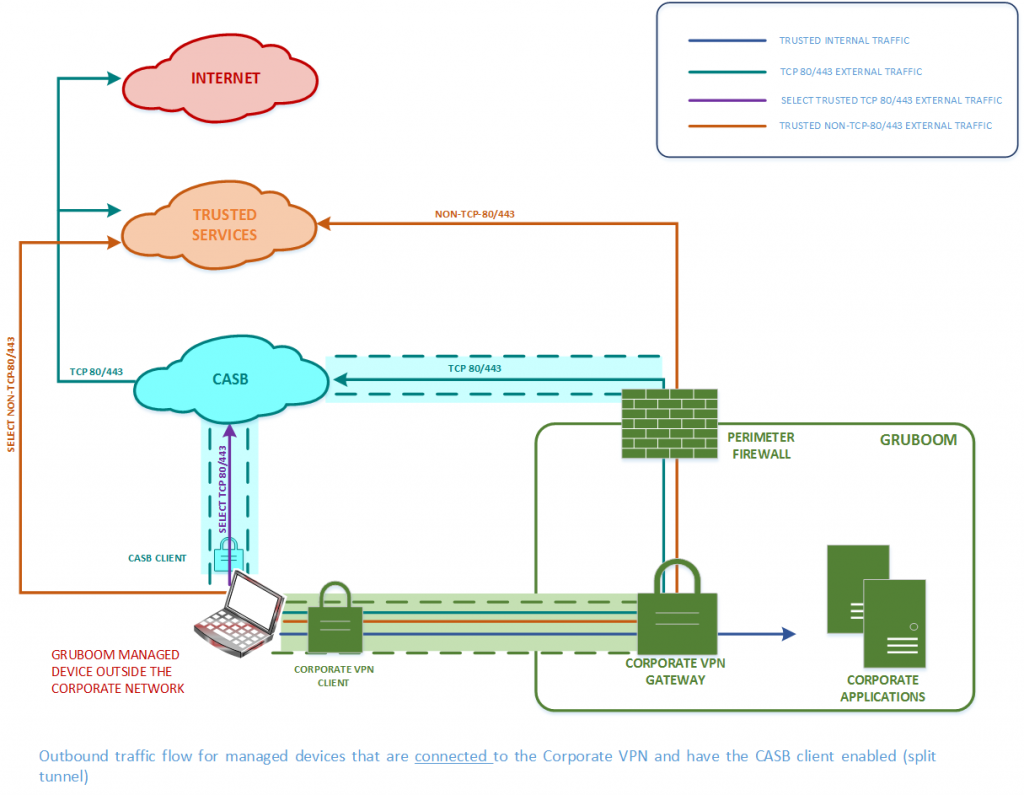
The above solution addressed the remote working challenges as follows:
- Provides a better user experience for trusted public cloud applications as our CASB provider also uses geolocation to egress to an edge location closest to the user, thereby minimizing latency.
- Provides a better user experience for real-time media traffic by ensuring that such traffic avoids tunnels (both CASB and Corporate) and egresses directly out of the user’s local Internet connection.
- Allows the application of DLP and Threat Management Policies within the CASB cloud as well as on the Corporate perimeter firewalls for all non-media traffic. Well, enforcing Security across different products (CASB + Corporate Firewall) is also a challenge and that can be addressed by product consolidation/integration.
NOTE:
- In order to ensure the Security of the managed device, the Corporate VPN must be AlwaysOn so that the split tunnel and CASB solution are always enabled on a remote worker’s managed device.
-
For real-time media clients using the ICE protocol (e.g. Skype, Teams), peer-to-peer communication between clients will always prefer the direct path and when one of the clients is on a remote worker’s managed device, the peer-to-peer audio/video communication will traverse the Corporate VPN, thereby leading to poor audio/video quality. In order to prevent this, either the Corporate VPN or firewalls on the managed devices must be configured to prevent such peer-to-peer media traffic from traversing the Corporate VPN and instead egress directly out of the user’s local Internet connection to media relay services on the Internet.

Thanks for that guys!